As of August, 2015
| Faculty/Department | Department of Information Network Systems Graduate School of Information Systems |

|
| Members | Satoshi Ohzahata, Associate professor | |
| Affiliations | IEICE, IPSJ, ACM, IEEE | |
| Website | https://www.net.lab.uec.ac.jp/ | |
Network, Internet, Wireless communications, Wired communications, Wireless networks, Wireless LAN, Cross-layer controls, Traffic controls, TCP/IP, Network coding
Many smartphones, tablets, notebooks, and other mobile devices are equipped with multiple wireless interfaces. By using the wireless interfaces, mobile device users are able to access the Internet anywhere, anytime and obtain text, image, audio, and other information content.
However obtaining the content via wireless networks is not always a convenient process. More than a few users have experienced of very long download times and streaming videos that freeze repeatedly during playback.
There are two conceivable methods to make it faster and more convenient to access information content via networks (see Figure 1). One is increasing the physical speeds of networks. The other is increasing the usage efficiency of networks. Associate Professor Ohzahata’s laboratory is engaged in researching the latter method.

The Internet connectivity technologies were originally developed for wired networks. The most common the Internet connection in the 1990s was the wired local area network (wired LAN). The primary device people used to access the Internet was the computer, which was almost always connected to a wired LAN (Ethernet) by a metal cable. The basic connectivity technologies were Ethernet and TCP/IP.
A key advantage of wired networks is the reliability of their physical connection. Communicated data are first divided into small units called packets before being transmitted. With wired networks, very few packets are lost during transmission.
Wireless networks, on the other hand, have no physical cable. Packets are transmitted by radio waves that propagate through the air. Therefore, the connection between the device and the network is less stable than a wired connection. Packets are often lost along wireless Internet connections due to noise propagating through the atmosphere. When a packet is lost, the data must be re-sent. As a result, compared to wired Internet connections, wireless connections tend to have slower effective data transmission speeds and consume more power per unit of data.
The most common connection to the Internet today is the wireless local area network (wireless LAN). Smartphones, tablets, and other devices essentially connect to the Internet by either wireless LANs or the mobile phone system. They are not even equipped with wired network interfaces. And while notebooks still have wired network interfaces, most actually connect via wireless networks.
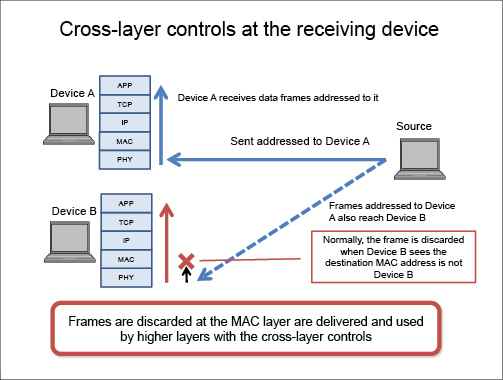
The problem here is that generally only one connection channel at a time can be maintained on a wireless LAN. When an access point (transmission server) covers two or more devices, data are transmitted by switching in order through the devices being communicated to.
Because only one communication channel is established at a time, excess communications take place. For example, if an access point is sending the same data to two devices, the data are sent twice to each device. What’s going on in this case is that when a device receives a data packet intended for the other device, the device discards the data packet because the data packet is not addressed to it.
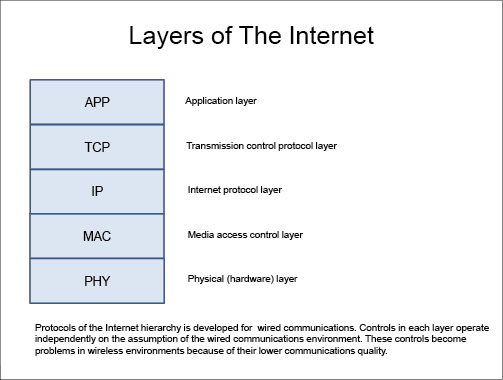
Networks, whether wired or wireless, have a hierarchal structure (see Figure 2). At the bottom of the hierarchy is the physical layer where data are sent and received electrically, above which is the MAC layer that controls access to the network. The MAC layer is followed by the IP layer and TCP layer, and the very top layer of the hierarchy is the application layer. Devices initially receive all data packets, even those not addressed to them, on the physical layer. At the MAC layer, devices determine whether a data packet is addressed to them and discard those that are not.
The Ohzahata laboratory is working on making it possible to receive data simultaneously at two devices by introducing controls that span multiple network layers (cross-layer controls) (see Figure 3). With these controls, data communications require just one transmission, which raises the effective data transfer speed and reduces power consumption.
Another difficulty is that when one data content is divided into several pieces and downloaded by multiple devices, near the end of the download, different devices often need different pieces to complete the download. Normally, this necessitates sending each different piece individually. This increases the number of transmissions needed, extends the waiting time until the transfer finishes, and raises power consumption.
To alleviate this issue, the Ohzahata laboratory is researching technology that will reduce the number of transmissions by coding the data pieces in advance and sending the coded pieces simultaneously to multiple devices.
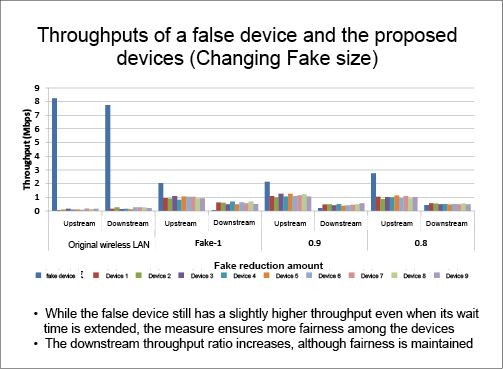
The laboratory is also attempting to defeat priority-faking on devices that manipulate the priority levels of other devices at the access point (transmission server). Normally, all devices have the same priority level, and the access point randomly determines which device to next start communications with. However, if a device falsely uses a high priority level, it will secure the communication channel faster than other devices. When such a device is present on a network, other devices will face longer wait times and see their effective data transfer speeds drop noticeably. The laboratory’s research is working on having access points deliberately extend the wait time for devices falsely uses a high priority level so that there is no bias in the data transfer speeds among devices (see Figure 4).
A future research area being considered is easing network congestion by recommending of similar alternatives. For example, you want to download some data from a Website but you cannot connect to the server because of network congestion. When this happens, the network will guide you to another Website that has similar data. This approach will ease congestion and prevent servers from going down.
[Interview and article by Akira Fukuda (PR Center)]